Introduction
A control panel in web hosting, is an interface provided by the hosting company that allows users to manage their web server from a single place. Control Panels are available for servers running both Windows and Linux operating system. Web-based control panels usually have a graphical interface and tool suite designed to make the process of hosting a website more manageable and simpler.
Role of Control Panel in a Virtual Server Hosting
Virtual Server Hosting also known as VPS (Virtual Private Server) is known for its flexibility and bridges the gap between Shared Hosting and Dedicated Servers. VPS hosting is an excellent solution for websites where the owner must have full control over their web server and resources. For controlling a Virtual Server Hosting account, a control panel can come in handy and make the administration easier.
What’s Included in the Functionality of Control Panel?
- Server logs – It is a log file which contains the list of activities performed by the server. It is automatically created and used by the system administrator to examine page requests, traffic patterns and helps in fine tuning site administration.
- Resource reports – With the control panel, a system administrator can view the availability of resources including available space, bandwidth, and used space. It is essential for businesses who are scaling and following a hyper-growth approach.
- Configuring and maintaining email accounts and user accounts – A control panel aids in the management of various email accounts associated with the website.
- Database management, user access, data manipulation – With a control panel like cPanel or Plesk, a system administrator can manage a database that contains website pages, images, and user information. Any changes required to the database are also managed with a control panel.
- Web log analysis software – A system administrator can parse a server log file from a web server and analyze it thoroughly with the control panel. It is also known as web log analyzer and can be used to extract and analyze user data viz. a number of visits, unique visitors, rush hours, authenticated users, OS used, browsers used, robots used, HTTP errors and more.
- File Management – Hosting account files and website files is managed from the control panel.
Plesk and cPanel as Control Panel Solutions
For system administrators, webmasters and IT users; the choice of operating system is a matter of preference. The same goes for control panels. The two most popular control panels, viz. cPanel and Plesk have their dedicated user base. Furthermore, both have their own set of pros and cons as well.
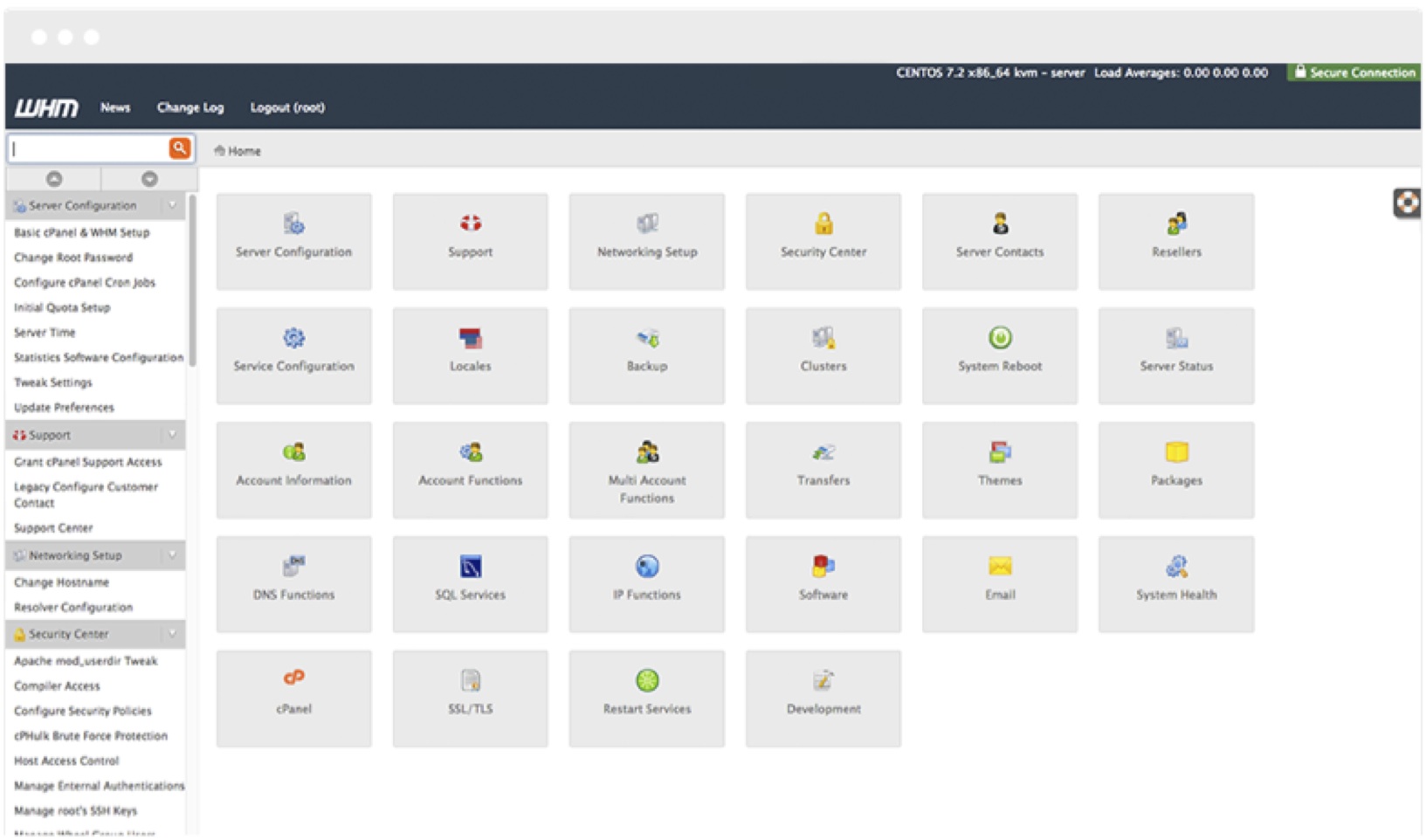
WHM/cPanel
cPanel is a Linux based web hosting control panel with a simple graphical interface and automation tool designed to make web hosting and web servers easier to manage. Based on a three-tier structure, cPanel is tailored to function to suit the needs of system administrators, resellers, and end-user website managers. The site management and server administration is done through a web browser.
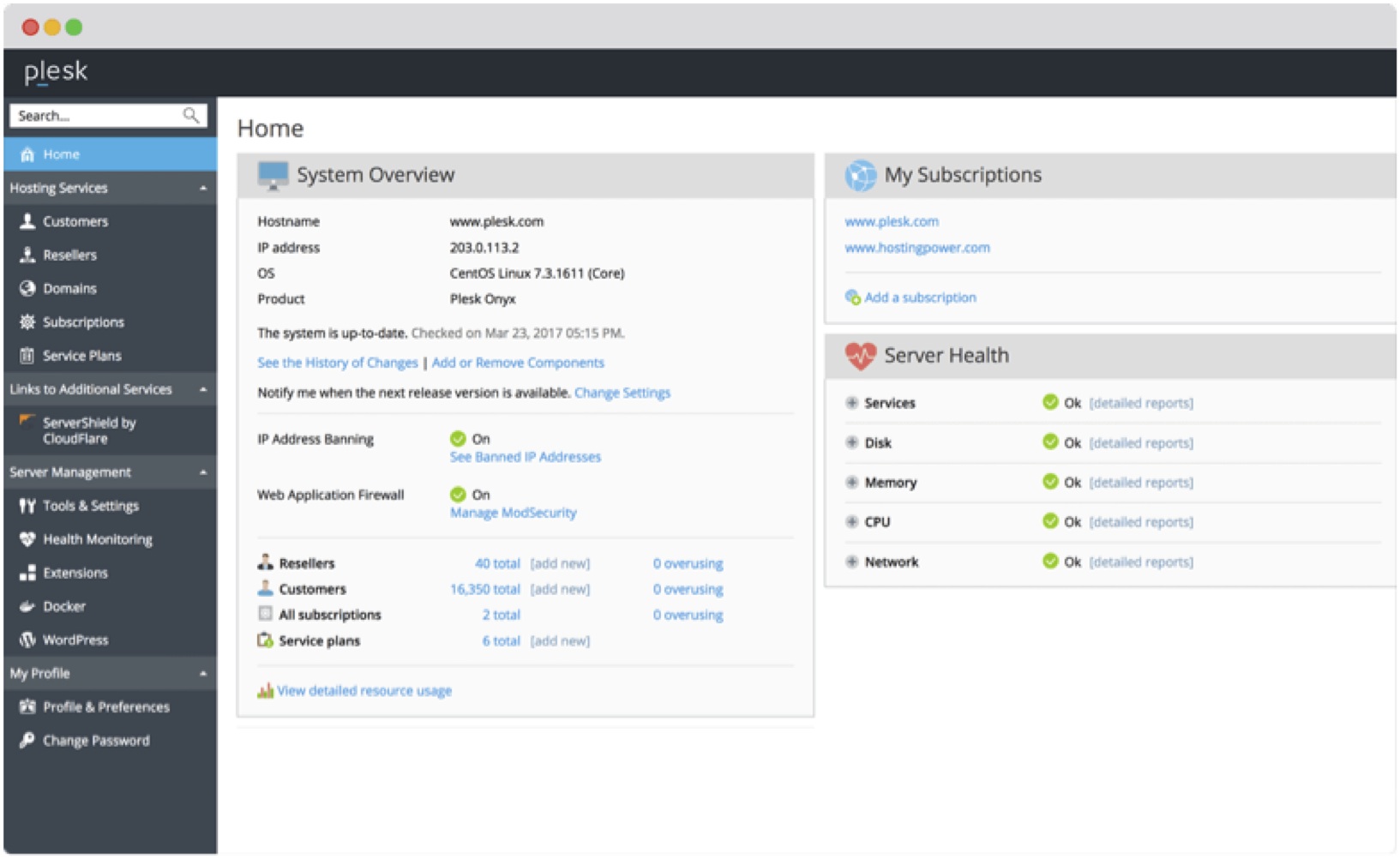
Plesk
Plesk, also known as Parallel Plesk Panel, offers web hosting service providers and virtual server hosting users the ability to configure and maintain both Windows and Linux servers. It is a flexible, effective and secure control panel for administrators to meet a broad range of requirements.
Panel Features
- Command Line Access
Command Line Access is provided in both cPanel and Plesk. However, cPanel offers both command line access and API-based access which enables interaction with third-party software. Plesk, on the other hand, provides Panel Action Log Command Access Tool.
- Administration
System administrators can automate administration processes with control panels. cPanel is designed to function either as a Virtual Private Server or a Dedicated Server.
Both cPanel and Plesk support installation on CloudLinux, CentOS, Red Hat Enterprise Linux, however, only cPanel works flawlessly on Linux operating systems. Furthermore, only Plesk can be installed on Windows Server 2008 SP2, Windows Server 2008 R2 SP1, and Windows Server 2002.
- Plesk and cPanel support MySQL, PostgreSQL, PHPMyAdmin
- Email services for cPanel include IMAP, POP3, and Exim, while Plesk supports Qmail
- Removing Panel
Removing a control panel is possible however, it is not recommended. It requires formatting the server and reinstalling the operating system. There are certain uninstall scripts available, for both Plesk and cPanel, but it is not advisable because users will lose all their account data. Removing cPanel will remove all user sessions, suspended info, web logs, bandwidth files, DKIM keys and Crontab.
- Ease of Use
At the user level interface, cPanel aggregates functions into groups that include mail, preferences, logs, files, domains, security, databases and software services. Alternatively, Plesk is divided into functions that include statistical and resource usage, mail, users, websites and domains, statistics and applications.
- Handling Support Requests
With cPanel’s interface, you can access support services from their web host by email. However, this service must be supported by your web host.
Plesk has a detailed support request form where you must fill comprehensive information about the product version, work environment, OS version and the issue.
Multi-Level Clustering
- Plesk does not support multi-level clustering natively and requires Plesk Automation Services add-on to perform such tasks
- Loading Speed – Plesk may cause loading to occur at a slow speed than cPanel, and can become particularly slow on Linux servers
- Database Access – With Plesk, the database is accessed via Web admin. You can manage MySQL or MS SQL databases through a web browser. For cPanel, you can access PHPMyAdmin and manage MySQL databases
Comparison Chart
|
Parameters |
cPanel |
Plesk |
| Statistical Features | ||
| Services | Webalizer, AWStats, Analog | Webalizer, AWStats, Plesk Traffic Manager |
| Other Features | Graphical Analysis, Custom Reports, Logs | Real Time Bandwidth, Graphical User Breakdown, Custom Reports |
| DNS Features | ||
| Services | BIND | BIND |
| Other Features | Clustering and Hands-off automatic configuration | SOA Settings, Remote DNS, Load Balancing Support, DNS Recursion, Master/Slave Management, Automated File Matching |
| FTP | ||
| Services | PureFTPd and ProFTPd | ProFTPd |
| Other Features | Graphical File Manager, Drive Letter Access, Anonymous FTP, | Anonymous FTP, FTP Throttling, File Manager, Upload Directory |
| Database Support | ||
| Services | Postgre SQL, MySQL | Postgre SQL, MySQL |
| Admin Panels | phpMyAdmin, phpPgAdmin | phpMyAdmin, phpPgAdmin, Multi-user/Multi-DB |
| Mail Features | ||
| Services | Courier-IMAP, Courier-POP, Exim | Qmail |
| Mail List | Mailman | Mailman Aliasing, Groups, Auto-responses |
| Webmail | Horde, SquirrelMail | Horde IMP |
| Anti-Virus | ClamAV | DrWeb, Kaspersky |
| Anti-Spam | SpamAssassin, Spam Box, BoxTrapper | SpamAssassin |
| Web Features | ||
| Web Servers | Apache | Apache |
| Scripting | Apache, CGI-PERL, PHP, JSP, SSI | PHP, Python, SSI, CGI, Ruby, FastCGI |
| Development Tools | FrontPage | ColdFusion |
| Access | IP Deny Manager, Anti-leech, Hotlink Protector | – |
| Security | SSL, SuPHP, mod_security, phpSuExec | SSL, SuExec |
| Errors | Custom Error Pages, Last 300 Errors | – |
| Account | ||
| Reseller Login | Yes | Yes |
| Domain Owner Login | Yes | Yes |
| Mail User Login | Yes | Yes |
Conclusion
cPanel and Plesk are two of the most popular control panels, and both have their share of pros and cons. One must consider their operating system, server configuration, security needs and access control as well as usability preferences before opting for either of them. Both control panels have robust security options and are powerful administration tools. The final choice depends on the features that most closely adapt to your working environment.